
Software development has always involved procedures that work in sequence or follow a periodic order. The best ideas or the ideal response to specific concerns usually come first. After that, the process continues through the actual delivery or even ongoing maintenance of the finished product. This process of developing an application from scratch can be considered to be an effective part of the software development lifecycle (SDLC). SDLC is often taken as a complex process and when these complexities are not addressed, the goals of the process get delayed. Following particular SDLC best practices can help software development service providers with a defined procedure and will be beneficial to the development team too.
The Software Development Life Cycle is adopted by many businesses and it is among the popular methods of software development. This brings us to a point where understanding and implementation of SDLC has helped many businesses in streamlining and simplifying their business needs and functions. Also, partnering with software development services companies can help you rise above peers by following standard procedures. In this process, let us now understand which problems SDLC is able to solve.
1. Which Problems Get Solved by Incorporating Secure SDLC?
New vulnerabilities are frequently found in software that has been released, is integrated with so many partner products, and is available to end users. This is one issue with insecure code. Because developers are less focused on the code context, fixing security vulnerabilities that have already surfaced in the wild takes more time and effort. Without an SSDLC, programmers spend time repairing bugs rather than concentrating on releasing new features.
The issue of persistent developer security mistakes is likewise addressed by a SSDLC. The process identifies and fixes such recurring problems and offers fixes rapidly enough to be put into practice before the software is released for use in the real world. The lack of a security standard leaves clients with no way of knowing whether their product is secure, which is the final issue that a secure SDLC addresses. By standardizing the development lifecycle, businesses are free to apply any method to simplify the software development process. If you still aren’t sure, then here are some of the SDLC best practices for you to make you understand how following the best practices can deliver the best results.
2. 10 SDLC Best Practices to Implement Right away!
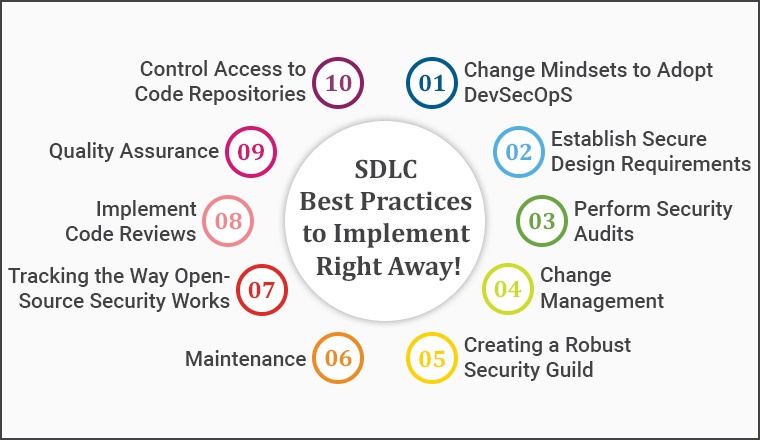
2.1 Change Mindsets to Adopt DevSecOpS
Considering security at an early stage of the SDLC process will certainly eliminate future bugs or flaws. Generally when security is considered, it is always taken into account in the later stages as a part of the last step of testing(i.e before deployment). But during the last stage, since there are a lot of other aspects too that need to be contemplated and so security becomes the last shot. With DevSecOps, security risks are examined in the coding stage during code reviews, penetration testing, or any other type of testing which can save the app from untimely errors and expected delivery dates.
A development team can significantly lower the cost of security and security failures by integrating security into earlier stages of the SDLC. When we use DevSecOps, no code has been added on top of a security flaw.t is much less expensive and simpler to correct at the design or implementation stages. It can be piece together as a workable solution when patching with other functions of the process.
2.2 Establish Secure Design Requirements
One of the most effective secure SDLC best practices is standardization. It promotes continual improvement when integrating security and it gives a predictable path for developing secure code. The easiest way to standardize is to include recommendations for security best practices in design requirements for new code. Approve tools for different stages of the software development lifecycle that will remind developers what to include at each stage. A test plan describes the following in a safe software development life cycle:
- The method for testing an application security testing
- Resources to be utilized
- Testing setting
- The restrictions with possible testing
- The anticipated testing activity schedule.
- During this phase, the team leader for quality assurance often plans tests and manages resource allocation.
2.3 Perform Security Audits
When meticulously planned and promptly carried out, security audits can be both time and cost-effective. With the use of these audits, you can find problems before they become serious problems that demand more resources to fix. A tried-and-true checklist streamlines and expedites the procedure.
The steps taken to ensure product security will have an impact on the cost of security testing services, the degree of control, and the amount of time needed to correct errors.
Determining your product’s susceptibility to assaults requires security testing. Make sure security procedures and tools are in place both at the beginning and throughout the development process. Clearly defining the functional needs of your development teams, taking into account typical security flaws, and planning appropriately is also essential.
2.4 Change Management
In any software development process, changes are an inevitable part of businesses. Client needs may change throughout the project and the reasons can be many, some of them are listed below:
- Since the time of the project’s inception, the business landscape has been completely evolving. The client developed a novel business concept that calls for distinctive remedies.
- Missing analysis of already-used procedures
- Inaccuracies in descriptions or a lack of comprehension of the client’s expectations;
- Unsatisfactory outcomes of interim tests performed while the project was being implemented.
Because of all these discrepancies, these attributes are needed to take care of. When a project is being launched or developed, the requirements are liable to change over time. It might be due to a shift in user or customer expectations, a change in how company needs are being met, or a failure to foresee a conflict in time. Instead of opposing change, you should establish control mechanisms to accommodate significant changes without impairing current operation. A Change Control Board is absolutely necessary to deny or approve changes and guarantee a smooth addition of change to the plan and schedule.
2.5 Creating a Robust Security Guild
Although there are many applications being developed, there are not many application security experts. Application security program implementations cannot scale even with automated static, dynamic, and interactive application security technologies. Developers are driven to learn new things and do the right thing. Your developers will benefit from identifying a group of developers who are interested in security and giving them instruction on both basic security issues and particular tools and approaches they may utilize.
Set up meetings with the team members to improve the program’s problematic areas. There are two advantages. The application security program’s first step involves expanding participation. Second, it helps both sides comprehend the difficulties and problems faced by the opposing group. In this process, you must make the testing phase an inevitable part of the SDLC process. The security and development teams understand the role testing plays.
As part of the testing process, security testing should be performed utilizing automated DevSecOps technologies to enhance application security.
Keep in mind that the DevSecOps methodology requires continuous testing throughout the SDLC. The greatest method to ensure that your goods and SDLC are secure from the start is to test frequently and early. This implies that teams should begin testing early in the development process and that security testing doesn’t end with deployment and implementation.
2.6 Maintenance
To avoid any ambiguities when the processes are being carried out, all security suggestions and rules should be communicated in explicit terms.
Including industry standards for security: To make sure that no potential for error goes unchecked, developers must abide by the compliance methods and guidelines that are generally accepted in the industry.
Roles for responsibility in software security: It is necessary to appoint a security team to conduct regular quality checks, such as threat modeling, and to evaluate every phase of software development.
Streamlined demands for developers: The developers must be able to understand the customer needs in order to provide SDLC that is free of errors and strongly secured. To prevent any ambiguity during the execution of the processes, all security suggestions and guidelines should be made explicit.
Time to choose an effective software architecture: A solidly safe SDLC depends on decent software architecture. Potential risks associated with the software development project can be prevented from security vulnerabilities if the architecture is taken into consideration beforehand. In case, businesses aren’t sure what to include as a part of your software architecture then here’s what can help.
How to choose a sound software architecture:
The foundation of a strong and safe SDLC is solid software architecture. The software system is completely evaluated by a robust software architecture that has the appropriate architectural pattern and defines quality attributes, such as scalability, resolvability, adaptability, resilience, etc.
Further Reading on Software Architecture:
What is Software Architecture?
2.7 Tracking the Way Open-Source Security Works
The risks of open source components with known vulnerabilities need to be addressed in order to provide a secure SDLC. Since 60 to 80 percent of the code in today’s software products is open source, it’s critical to focus on open source security management throughout the SDLC. Tools for measuring open source usage are automated technology called Software Composition Analysis (SCA) tools. They provide actionable prioritization and remediation insights as well as automated solutions. They can warn developers in real-time to all open source risks that develop in their code.
2.8 Implement Code Reviews
If you are working with Agile teams, you would know that these teams are different from the ones we work with regularly. On the other hand, one can benefit greatly from the decentralization of work within the team. The agile methodology allows every stakeholder involved in SDLC to check the security aspect. Thus, you can have multiple phases of security for a defined product. Though, the original outcomes will be shared by the developer who is in the right position to offer constructive criticism and appraisal as new features are added to the current code.
A code review checklist is a predetermined collection of guidelines and questions that your team will adhere to throughout the code review procedure. That gives you the advantage of an organized method for doing necessary quality checks before you approve code into the codebase.
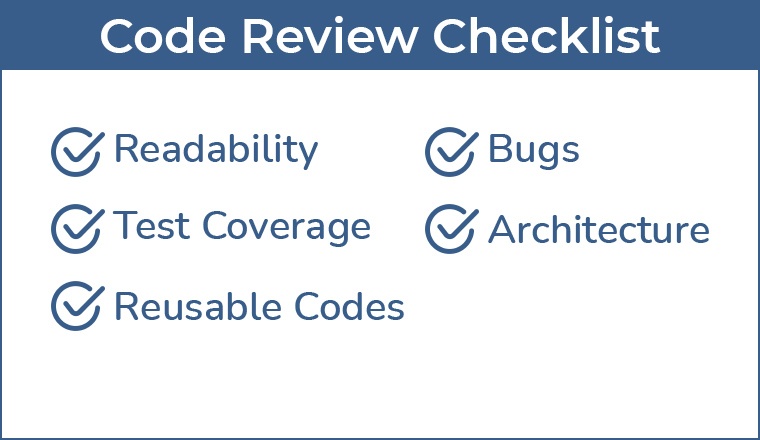
Any reviewer of code who is likewise exposed to the complexity knows the problems and understands which particular portion of the code base needs correction. Thus, the code reviewer benefits from the original creator of that section of the code base’s knowledge. When a final estimate is based on several accurate inputs, the estimate is always stronger and more dependable software solution.
2.9 Quality Assurance
In an ever-evolving software product, QA aids project teams in finding inconsistencies, system flaws, and feature redundancy. The following are the main reasons why effective QA procedures are crucial for the success of software projects:
- Serious failures in production applications are avoided.
- Brand value is damaged as a result of a bad customer experience.
- The invested money is lost as a result of system flaws.
- Decreased community, user, and developer involvement.
Because of all these reasons, businesses might feel the need for QA within their software development projects. The need for secure code will stave off security risks. You use security tools or use automated testing to improve code quality in a faster and more efficient way. Other than tools, it is also important for engineers to take care of quality before delivering. This needs to be instilled in the development teams.
Raising the appropriate questions and facilitating the debate around them in an open, honest, and powerful manner are the most crucial things one can do to foster a good QA mentality in a project team. When thinking about QA responsibilities, the testing phase is often the first thing that comes to mind.
With Quality assurance in place, you can complete the project more quickly and smoothly. Best practices can be useful in determining whether a project is ready for a successful delivery or stage thanks to effective tools based on quality measurements and defect tracking. To make sure that the design, requirement, test plan, code, and other papers and deliverables are in place, you need to define project goals and metrics. Actually, renowned experts who can do a quality audit of the projects also include quality analysts and representatives in consideration.
Further Reading on Quality Assurance:
Benefits of Quality Assurance For Your Business
2.10 Control Access to Code Repositories
When you are building an application, there are several new vulnerabilities as a part of secure applications. You can prefer to perform continuous integration, apply testing procedures or do anything that improves software design and integrate security. Businesses need access to development environments where they can insert and correct malicious codes. Controlling access to code repositories is one of the project goals which would ensure validated access and submission to code repositories. This will make it more difficult for hackers to hack it from any other source.
3. Conclusion
Finally, we can say that security is an indispensable aspect of SDLC, and the price to create secure applications and software will be much easier if we take care of the following measures we discussed in the blog. It isn’t a challenge if you know the right procedure for security tests and perform it at regular intervals. Secure SDLC is capable of offering faster deliveries, accuracy in the product, and minimal effort and time in developing software. Thus, it is safe to say that an ounce of prevention will provide pounds of protection to the businesses.




Comments
Leave a message...